VADA is dedicated to delivering superior analytics solutions while ensuring the utmost security of our client’s business data. This document outlines our commitment to achieving SOC 2 compliance, focusing on platform security to protect our clients’ sensitive information.
This security outline covers all aspects of platform security at VADA, including infrastructure, application, data storage, access controls, and incident response. Our goal is to ensure that client data is protected from unauthorized access, breaches, and other security threats.
By adhering to the SOC 2 Trust Service Criteria, VADA aims to demonstrate our dedication to maintaining a secure, reliable, and trustworthy platform. This not only safeguards client data but also reinforces our commitment to delivering high-quality analytics services that our clients can depend on.
I. Security Governance and Risk Management
1. Policies and Procedures
VADA has established a robust set of security policies and procedures to guide our security governance framework. These policies are designed to align with industry best practices and regulatory requirements:
Information Security Policy: Developed using frameworks like SOC 2 Type II and ISO 27001, this policy outlines our approach to managing and protecting client data. It is reviewed annually to ensure it meets current standards.
Access Control Policy: Defines protocols for granting, reviewing, and revoking access to systems and data. This policy is enforced through role-based access control (RBAC) and attribute-based access control (ABAC) systems.
Data Protection Policy: Specifies measures for handling, storing, and transmitting client data securely, incorporating guidelines from GDPR and CCPA.
Incident Response Policy: Details procedures for responding to and managing security incidents, including a structured incident response plan developed with input from industry experts and aligned with the NIST Cybersecurity Framework.
2. Risk Assessment
VADA conducts comprehensive risk assessments to identify, evaluate, and mitigate potential security threats:
Identification: Using asset management tools like Qualys to catalog and classify assets, data, and systems that require protection.
Evaluation: Assessing risks using threat modeling techniques and tools such as the OWASP Threat Dragon, focusing on the potential impact and likelihood of identified risks.
Mitigation: Implementing controls and safeguards based on risk assessment findings, including applying security patches and enhancing security configurations.
Monitoring: Continuously monitoring the environment with tools like ELK and Security Information and Event Management (SIEM) systems as Wazuh to detect incoming threats and vulnerabilities.
Risk assessments are conducted at least annually and whenever significant changes occur in the operational environment.
II. General Access Controls
1. User Access Management
VADA employs a comprehensive user access management framework to ensure that only authorized personnel have access to sensitive client business data:
Authentication Mechanisms:
Password Policy: Enforces a strong password policy requiring a minimum length of 12 characters, complexity (including upper and lower case letters, numbers, and special characters), and regular updates every 180 days.
Certificate-Based Authentication: Utilizes digital certificates and private keys for user and system authentication. This method involves issuing certificates through a Public Key Infrastructure (PKI) and leveraging them for secure access to systems and data.
Account Provisioning:
Identity and Access Management (IAM): Uses IAM solutions like Microsoft Azure Entra ID (formerly Active Directory) and LDAP (Lightweight Directory Access Protocol) for streamlined user account creation, management, and deactivation based on job roles and responsibilities.
Automated Workflows: Implements automated workflows to ensure timely and accurate provisioning and deprovisioning of user access.
Access Requests and Approvals:
Access Request System: Manages access requests through a centralized system such as Jira Service Management, requiring documented approvals from supervisors or designated approvers.
2. User Access Controls
To enhance security, VADA employs both Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) on many of the underlying services:
Role-Based Access Control (RBAC):
Role Definitions: Defines roles and associated permissions using LDAP and/or self-developed Authorizer service, ensuring users have access only to the resources necessary for their role.
Least Privilege Principle: Applies the principle of least privilege by restricting user access to the minimum necessary level for their job functions.
Attribute-Based Access Control (ABAC):
Policy Engine: Utilizes self-developed Authorizer service to enforce access controls based on user attributes (e.g., department, job title) and resource attributes (e.g., sensitivity level).
Dynamic Access Control: Implements dynamic access policies that adjust permissions in real-time based on contextual attributes like user location or device type.
3. Periodic Access Reviews
Regular reviews of access rights are conducted to ensure that permissions remain appropriate as roles and responsibilities change:
Quarterly Access Reviews: Conducts thorough reviews of user access permissions every quarter to identify and revoke unnecessary access.
Automated Audits: Utilizes automated tools to continuously monitor and audit access permissions, ensures compliance with access control policies.
Adjustments and Revocations: Promptly adjusts or revokes access based on changes in job roles, terminations, or other relevant events.
4. Access Control Technologies
VADA employs a variety of technologies to enforce access controls effectively:
Directory Services:
Azure Entra ID: for centralized management of user identities and access permissions.
LDAP: Implements LDAP (Lightweight Directory Access Protocol) directories for managing user access and authentication in certain systems.
Self-developed Authorizer service: All requests to the core of the system require to go through Authorizer service to be granted the necessary access.
Access Control Lists (ACLs): Configuring ACLs on critical systems (such as databases) and repositories to enforce granular access permissions.
5. Training and Awareness
Ensuring that all employees understand the importance of access controls and how to adhere to them is crucial:
Security Awareness: Conducts regular training sessions on access control policies, procedures, and best practices.
Phishing Awareness: Implements phishing awareness programs to educate users on identifying and avoiding phishing attacks that could compromise access credentials.
By implementing comprehensive user access management practices, enforcing role-based access control, conducting periodic access reviews, leveraging advanced access control technologies, and promoting security awareness, VADA ensures that access to client business data is strictly controlled and monitored. This rigorous approach helps to protect sensitive information from unauthorized access and potential breaches.
III. Network and Infrastructure Security
1. Firewalls and Perimeter Security
VADA employs robust perimeter security measures to protect the network infrastructure from external threats:
Firewalls: Deploys firewalls to monitor and control incoming and outgoing network traffic based on predetermined security rules.
Intrusion Detection and Prevention Systems (IDPS): Utilizes IDPS to detect and prevent potential threats and intrusions in real time.
Network Segmentation: Segments the network into separate zones to limit the spread of potential attacks and restrict access to sensitive data.
2. Secure Network Architecture
A secure network architecture is essential to safeguard VADA’s infrastructure and client data:
Virtual Private Network (VPN): Implements VPNs to ensure secure remote access to the network.
Zero Trust Architecture: Adopts a Zero Trust approach, where no entity inside or outside the network is trusted by default.
Redundancy and Failover Mechanisms: Designs the network with redundancy and failover capabilities to ensure high availability and resilience against disruptions.
3. Encryption
Encryption is a critical component of VADA’s data protection strategy:
Data in Transit: Encrypts data transmitted over networks using Transport Layer Security (TLS) and mutual TLS (mTLS) to protect it from interception and tampering. mTLS adds an additional layer of security by requiring both client and server to authenticate each other, ensuring that data is transmitted between trusted parties.
Data at Rest: Encrypts stored data to prevent unauthorized access in case of a data breach.
4. Public Key Infrastructure (PKI)
To support secure communications, VADA implements a robust Public Key Infrastructure (PKI) to manage and distribute digital certificates. This ensures the authenticity and integrity of communications by:
Certificate Authority (CA): Establishes a trusted CA to issue and revoke digital certificates.
Certificate Management: Implements processes for the generation, distribution, and renewal of certificates.
Key Management: Ensures secure storage and handling of private keys to prevent unauthorized access.
Certificate Validation: Uses Online Certificate Status Protocol (OCSP) and Certificate Revocation Lists (CRLs) to validate the status of certificates in real time.
5. Patch Management
VADA maintains a rigorous patch management process to keep systems up-to-date and secure:
Regular Updates: Ensures that all network devices, servers, and applications are regularly updated with the latest security patches.
Patch Testing: Tests patches in a controlled environment before deployment to prevent potential disruptions.
Automated Patch Deployment: Utilizes automated tools to deploy patches promptly across the systems.
6. Vulnerability Management
Proactively identifying and mitigating vulnerabilities is essential to maintaining network security:
Regular Scanning: Conducts regular vulnerability scans to identify and assess security weaknesses in the network infrastructure.
Penetration Testing: Performs periodic penetration tests to evaluate the effectiveness of security controls and uncover potential vulnerabilities.
Remediation: Implements a structured process for promptly addressing identified vulnerabilities and documenting remediation efforts.
7. Secure Configuration
Ensuring that all network devices and systems are securely configured is crucial for preventing unauthorized access and attacks:
Baseline Configurations: Establishes and enforces baseline security configurations for all systems.
Configuration Management: Continuously monitors and manages configurations to ensure compliance with security policies and best practices.
Hardening: Applies hardening techniques to reduce the attack surface by disabling unnecessary services and features.
8. Monitoring and Logging
Continuous monitoring and logging are vital for detecting and responding to security incidents:
Security Information and Event Management (SIEM): Implements SIEM systems to collect, analyze, and correlate security event data in real-time.
Network Monitoring: Continuously monitors network traffic for suspicious activities and potential security incidents.
Log Management: Maintains comprehensive logs of network activities and security events for analysis and forensic investigations.
By implementing robust network and infrastructure security measures, including firewalls, secure network architecture, encryption, patch management, vulnerability management, secure configuration, and continuous monitoring, VADA ensures the protection and integrity of its network infrastructure and client business data.
IV. System and Application Security
1. Secure Software Development Lifecycle (SDLC)
VADA ensures that security is integrated into every phase of the Software Development Lifecycle (SDLC) to minimize vulnerabilities and enhance overall application security:
Requirements and Design:
Security Requirements: Incorporates security requirements from the outset, ensuring that they are aligned with industry standards such as OWASP and NIST.
Threat Modeling: Uses tools like OWASP Threat Dragon or Microsoft Threat Modeling Tool to identify potential security threats during the design phase.
Development:
Secure Coding Practices: Enforces secure coding standards, such as those outlined by OWASP, to prevent common vulnerabilities like SQL injection and cross-site scripting (XSS).
Code Reviews: Implements peer code reviews and automated static code analysis tools such as SonarQube to identify and remediate security flaws during development.
Testing:
Automated Security Testing: Integrates security testing tools as Selenium into the CI/CD pipeline for automated vulnerability detection.
Penetration Testing: Conducts regular penetration testing using tools like Nessus to simulate attacks and identify vulnerabilities in the application.
Deployment:
Secure Configuration: Ensures that applications are deployed with secure configurations, following guidelines like the CIS Benchmarks.
Infrastructure as Code (IaC): Uses IaC tools like Terraform / Helm / Ansible to automate the secure deployment of infrastructure, ensuring consistency and compliance with security standards.
Maintenance:
Patch Management: Regularly applies security patches to applications and underlying systems using tools like Ansible to mitigate known vulnerabilities.
Vulnerability Management: Continuously monitors applications for new vulnerabilities using tools, and addresses them promptly.
2. Application Security Controls
VADA implements a comprehensive suite of security controls to safeguard its applications from a wide array of threats. These controls are designed to protect against vulnerabilities at various levels of the application stack, ensuring that client data and system integrity are maintained.
a. Web Application Firewalls (WAF)
VADA deploys Web Application Firewalls (WAFs) to provide a critical layer of defense against common web-based attacks such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
WAF Solutions:
Cloudflare: We use Cloudflare’s WAF to filter and monitor HTTP/HTTPS requests, providing protection against malicious traffic before it reaches the application. Cloudflare’s WAF is highly effective at blocking automated bots, DDoS attacks, and application-layer threats.
L7 Firewalls: L7 firewalls are deployed in proxy layers, to provide deep packet inspection and to enforce security policies based on the content of the application-layer traffic. These firewalls are crucial for detecting and mitigating advanced threats that could exploit application vulnerabilities.
Custom Rules and Policies: VADA configures custom WAF rules tailored to the specific needs of each application. This includes defining rules to block or challenge traffic based on IP reputation, geolocation, request rates, and other factors that indicate potential malicious intent.
Real-Time Monitoring and Alerts: The WAF solutions are integrated with our Security Information and Event Management (SIEM) systems, allowing for real-time monitoring and generating alerts when suspicious activity is detected. This integration enables rapid response to potential security incidents.
b. Secure API Management
APIs are a critical component of modern applications, and securing them is paramount to protecting data and application functionality.
API Gateways: VADA employs API gateways to manage, secure, and monitor API traffic. These gateways enforce authentication, rate limiting, and access control policies to protect against misuse and attacks like API scraping or abuse.
OAuth2 and JWT: For securing API access, VADA uses OAuth2 for authorization and JSON Web Tokens (JWT) for secure token-based authentication. These technologies ensure that only authorized users and applications can access the APIs.
Rate Limiting and Throttling: To prevent denial-of-service (DoS) attacks and abuse, VADA implements rate limiting and throttling policies at the API level. These controls restrict the number of requests a client can make within a given timeframe, protecting the backend services from being overwhelmed.
3. Code Integrity and Security
Ensuring Secure Development Practices: VADA integrates security throughout the software development lifecycle (SDLC) to minimize vulnerabilities in the application code.
Static Application Security Testing (SAST): Tools like SonarQube are used to perform static code analysis during the development process. This helps identify security vulnerabilities, such as buffer overflows or insecure API usage, early in the development cycle.
Dynamic Application Security Testing (DAST): VADA conducts dynamic testing using tools like OWASP ZAP to assess the security of applications in a running state. DAST helps identify vulnerabilities that may only be exploitable when the application is operational, such as runtime injection attacks.
Software Composition Analysis (SCA): VADA uses SCA tools to scan for vulnerabilities in open-source libraries and third-party components integrated into the application. This ensures that dependencies do not introduce known security risks.
4. System Hardening
VADA employs system hardening techniques to reduce the attack surface of servers, workstations, and other critical systems:
Baseline Configurations:
CIS Benchmarks: Adopts CIS Benchmarks for secure baseline configurations on all systems, ensuring they are hardened against attacks.
Configuration Management: Uses tools as Ansible / Helm / Terraform to automate the enforcement of secure configurations across all systems.
Minimal Installations:
Minimalist Approach: Ensures that only essential services and applications are installed on systems, reducing the number of potential attack vectors.
Regular Audits:
Configuration Audits: Conducts regular audits by Nessus to ensure systems remain securely configured and compliant with baseline standards.
5. Logging and Monitoring
Continuous logging and monitoring are essential to detecting and responding to security incidents:
Security Information and Event Management (SIEM):
SIEM Platforms: Implements SIEM solutions to collect, correlate, and analyze security logs in real-time, providing actionable insights and alerts.
Application Logging:
Centralized Logging: Ensures all applications log security-relevant events to a centralized logging system, enabling comprehensive monitoring and analysis.
Anomaly Detection:
AI/ML Tools: Utilizes AI/ML-driven tools as ELK stack to identify unusual patterns and anomalies that could indicate a security incident.
By integrating security throughout the SDLC, implementing robust application security controls, hardening systems, and ensuring comprehensive logging and monitoring, VADA effectively monitors and secures its systems and applications against threats, maintaining the integrity and availability of client business data.
V. Data Security and Privacy
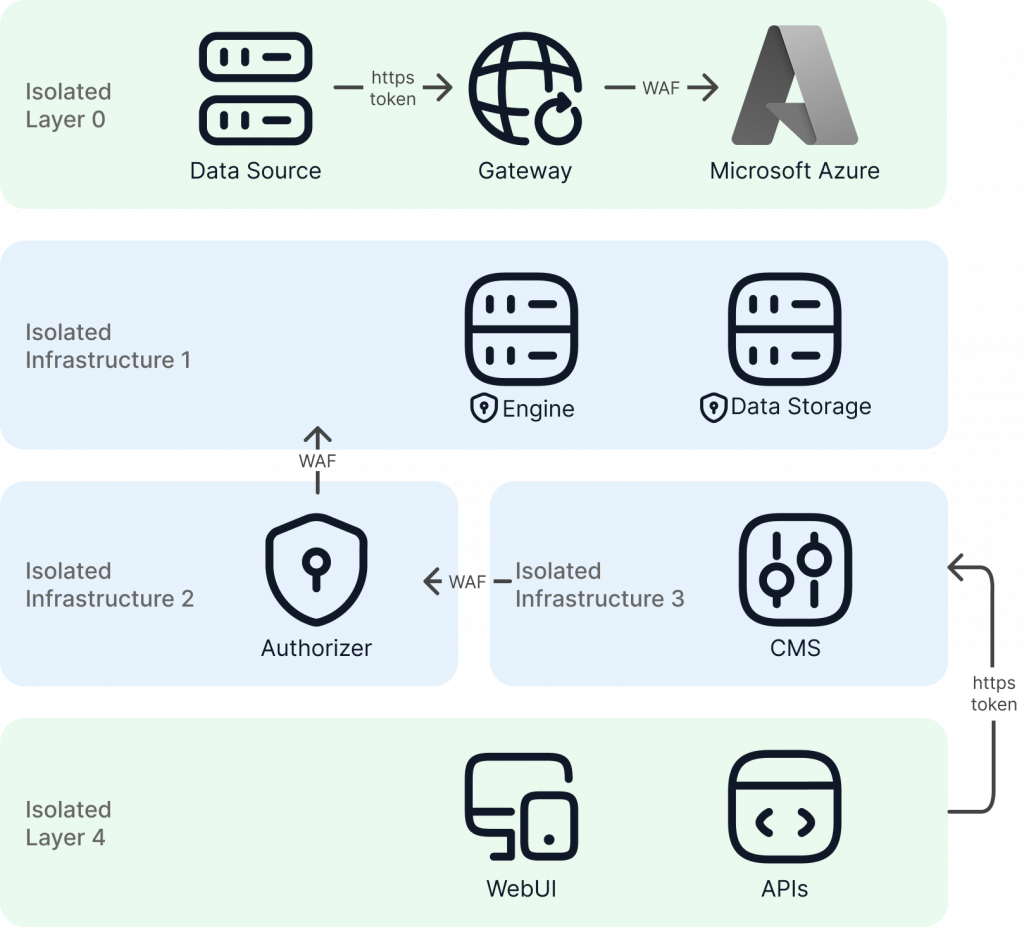
1. Data Classification
VADA implements a robust data classification framework to ensure that all client business data is appropriately identified, protected, and handled according to its sensitivity:
Classification Levels:
Public: Data that is non-sensitive and can be freely shared with the public.
Internal: Data intended for internal use within VADA, which is not meant for public disclosure.
Confidential: Data that is sensitive and restricted to specific employees, requiring strict access controls.
Highly Confidential: The most sensitive data, including client business data, that requires the highest level of protection and is accessible only to a limited number of authorized individuals.
Handling Procedures:
Data Handling Guidelines: Establishes detailed guidelines for the handling, storage, and transmission of data at each classification level, ensuring consistent protection across the organization.
2. Data Encryption
Encryption is a cornerstone of VADA’s data protection strategy, ensuring that client data remains secure both at rest and in transit:
Data at Rest:
Disk Encryption: Implements full disk encryption using tools to protect data stored on servers and storage devices.
Database Encryption: Employs Transparent Data Encryption (TDE) in databases to secure stored data.
File-Level Encryption: Utilizes file encryption tools such as GPG to protect individual files, ensuring that data remains secure even if unauthorized access is gained.
Data in Transit:
TLS/mTLS: Encrypts data in transit using Transport Layer Security (TLS) and mutual TLS (mTLS) to protect it from interception and tampering during transmission over networks between services.
VPN: Employs Virtual Private Networks (VPNs) to secure remote access connections, ensuring that data transmitted between remote users and the corporate network is encrypted.
Secure File Transfer: Uses secure file transfer protocols such as SFTP to encrypt data during transfer between systems.
HTTPS: Secures web-based communications by implementing HTTPS (HTTP over TLS), ensuring that all data transmitted between web browsers and servers is encrypted and protected from eavesdropping and man-in-the-middle attacks.
3. Data Retention and Disposal
VADA enforces strict data retention and disposal policies to manage the lifecycle of client data securely and responsibly:
Data Retention Policy:
Retention Periods: Defines retention periods for different types of data based on legal, regulatory, and business requirements.
Archiving Solutions: Uses archiving solutions such as Microsoft Azure Archive Storage to store data that must be retained for long periods, with access restricted to only authorized personnel.
Data Disposal:
Secure Data Deletion: Implements secure data deletion processes to ensure that data is irretrievably deleted when it is no longer needed.
Physical Destruction: For physical media, employs methods such as shredding or degaussing to ensure that data cannot be recovered.
4. Data Access Controls
At VADA, ensuring the security of client business data through stringent data access controls is paramount. We understand that unauthorized access to sensitive information can lead to significant risks, and therefore, we employ advanced measures to guarantee that only authorized personnel have access to this data.
Role-Based Access Control (RBAC)
Granular Access Management: VADA implements Role-Based Access Control (RBAC) to precisely manage access rights based on user roles within the organization. This approach ensures that users are granted the minimum level of access necessary to perform their job functions, adhering to the principle of least privilege.
Access Management Services: We utilize robust multi-layer services to define and enforce RBAC policies. These services allow us to assign roles to users, and tightly control access to critical applications, systems, and data based on those roles.
Custom Role Definitions: Roles are defined with fine granularity, tailored to specific job functions. For instance, an analyst might have read-only access to data, while an administrator might have broader access but still be restricted from accessing certain types of sensitive information.
Automated Role Assignment: Through integration with HR systems, role assignments are automated based on an employee’s job position, department, responsibilities and so on… This ensures that access rights are consistently applied and automatically updated as roles change.
Regular Role Reviews: Access rights and roles are reviewed periodically to ensure they remain appropriate as users’ responsibilities evolve. Automated tools can assist in these reviews, providing alerts for potential role creep or unnecessary access.
Attribute-Based Access Control (ABAC)
Dynamic and Contextual Access: In addition to RBAC, VADA implements Attribute-Based Access Control (ABAC) to further refine access permissions. ABAC allows access decisions to be made based on a combination of user attributes (e.g., device, location) and resource attributes (e.g., data classification level).
Policy-Based Management: ABAC policies are centrally managed and dynamically enforced. These policies consider multiple factors, including the user’s role, location, and the sensitivity of the data being accessed.
Context-Aware Access: ABAC allows for context-aware access control, where permissions can change based on real-time conditions. For example, access to highly confidential data might be restricted if a user is attempting to access it from an untrusted network or outside of business hours.
Advanced Scenarios: ABAC enables complex access control scenarios, such as allowing temporary access for specific projects or restricting access to sensitive data based on geographic location or device compliance status.
5. Privacy Compliance
VADA is committed to complying with all applicable data protection and privacy regulations, ensuring that client data is handled in a legally compliant manner:
Regulatory Compliance:
GDPR Compliance: Adheres to the General Data Protection Regulation (GDPR) requirements, including implementing data subject rights, conducting Data Protection Impact Assessments (DPIAs), and maintaining records of processing activities.
CCPA Compliance: Complies with the California Consumer Privacy Act (CCPA) by providing transparency, access, and deletion rights to consumers regarding their personal data.
Other Jurisdictional Laws: Ensures compliance with other relevant data protection laws, such as the HIPAA for healthcare data or the Australian Privacy Act, as applicable to VADA’s operations.
Privacy by Design:
Privacy Integration: Incorporates privacy considerations into the design and development of systems and processes from the outset, following the principles of Privacy by Design.
6. Data Audits and Monitoring
VADA conducts regular audits and monitoring to ensure data security and privacy controls are effective and consistently applied:
Data Audits:
Internal Audits: Conducts regular internal audits using tools like Netwrix Auditor to assess compliance with data security and privacy policies, identifying areas for improvement.
Third-Party Audits: Engages external auditors to conduct independent assessments of data security and privacy practices, providing an additional layer of assurance.
Monitoring and Reporting:
Data Activity Monitoring: Implements Data Activity Monitoring (DAM) solutions to continuously monitor access and usage of sensitive data, detecting and responding to suspicious activities.
Reporting and Analytics: Creates graphs to generate detailed reports on data access, usage, and compliance, providing insights that support ongoing improvement efforts.
By implementing these comprehensive data security and privacy measures, VADA ensures that client business data is protected throughout its lifecycle, from classification and encryption to access control, compliance, and monitoring. This commitment to data security and privacy helps maintain trust with clients and ensures compliance with regulatory requirements.
VI. Incident Management
VADA prioritizes the ability to swiftly and effectively respond to security incidents to minimize their impact and ensure the continued protection of client business data. Our incident management framework encompasses the entire lifecycle of an incident, from detection and analysis to containment, recovery, and post-incident review.
1. Incident Response Plan
Comprehensive Preparedness: VADA has developed and maintains a comprehensive Incident Response Plan (IRP) designed to address a wide range of potential security incidents, from minor breaches to major cybersecurity events.
Defined Roles and Responsibilities: The IRP clearly outlines the roles and responsibilities of each team member involved in incident response. This includes incident handlers, IT support staff, legal and compliance teams, public relations, and executive leadership. Each role is defined with specific actions to be taken during an incident, ensuring a coordinated and efficient response.
Incident Response Team (IRT): VADA has established an Incident Response Team (IRT) comprising cybersecurity experts, IT specialists, and key stakeholders. This team is trained and equipped to respond to incidents 24/7, ensuring rapid detection, containment, and mitigation of threats.
Incident Classification and Prioritization: The IRP includes a framework for classifying and prioritizing incidents based on their severity and potential impact on the organization and clients. This allows VADA to allocate resources effectively and ensure that critical incidents receive the appropriate level of attention.
2. Forensics and Analysis
Thorough Investigation and Root Cause Analysis: When an incident occurs, VADA is committed to conducting thorough forensics and analysis to understand the root cause and prevent future occurrences.
Digital Forensics Tools: VADA utilizes industry-leading digital forensics tools to investigate security incidents. These tools allow the IRT to collect, preserve, and analyze digital evidence from affected systems without compromising the integrity of the data.
Incident Analysis: The IRT conducts a detailed analysis of each incident, identifying the attack vectors, vulnerabilities exploited, and the extent of the compromise. This analysis is critical for determining the appropriate remediation steps and for informing future security measures.
Root Cause Identification: The forensics process aims to identify the root cause of the incident, whether it be a software vulnerability, human error, or a sophisticated attack. Understanding the root cause is essential for implementing effective long-term fixes and improving VADA’s overall security posture.
3. Communication and Reporting
Clear and Timely Communication: Effective communication is a cornerstone of VADA’s incident management process, ensuring that all stakeholders are informed and that the incident is handled transparently and efficiently.
Internal Communication Channels: VADA has established clear internal communication channels to keep the Incident Response Team, IT staff, and management informed throughout the incident response process. Secure communication platforms, such as encrypted messaging apps or dedicated incident response portals, are used to share updates and coordinate actions in real-time.
Client and Stakeholder Notifications: VADA is committed to promptly notifying affected clients and stakeholders in the event of a security incident that impacts their data or services. Communication plans include pre-approved templates for incident notifications, ensuring that messages are clear, accurate, and consistent. Clients are informed of the nature of the incident, its impact, and the steps being taken to mitigate and resolve the issue.
Regulatory Reporting: In cases where the incident triggers regulatory reporting requirements (e.g., under GDPR, CCPA, or other data protection laws), VADA ensures timely compliance with these obligations. The IRT works closely with legal and compliance teams to prepare and submit required reports to the appropriate authorities within the stipulated time frames.
Post-Incident Reports: After an incident is resolved, a comprehensive post-incident report is generated, detailing the events, actions taken, and lessons learned. This report is shared with relevant stakeholders, including clients when applicable, to provide transparency and to reinforce VADA’s commitment to continuous improvement in security practices.
By implementing these robust incident management practices, VADA ensures that it can respond quickly and effectively to any security threats, minimizing their impact and maintaining the trust and confidence of its clients.
VII. Business Continuity and Disaster Recovery
At VADA, the ability to maintain operations and swiftly recover from disruptions is critical to our commitment to providing reliable services to our clients. Our Business Continuity and Disaster Recovery (BC/DR) strategy is designed to ensure that the organization can continue to function in the event of a disaster or significant disruption, minimizing downtime and data loss.
1. BC/DR Plan
Comprehensive Planning for Continuity and Recovery: VADA has developed a comprehensive Business Continuity and Disaster Recovery (BC/DR) plan to ensure that the organization can quickly recover from unforeseen events and continue to operate effectively.
Business Continuity Planning (BCP): VADA’s Business Continuity Plan outlines the procedures and processes to be followed in the event of a disruption to normal business operations. This plan covers a wide range of scenarios, including natural disasters, cyberattacks, and system failures, and ensures that critical business functions can continue with minimal interruption.
Critical Business Functions Identification: The BCP identifies and prioritizes critical business functions that must be maintained or quickly restored in the event of a disruption. These functions include client services, data access, and communication systems.
Contingency Planning: The plan includes contingency measures such as alternative work locations, remote work arrangements, and manual processing procedures to ensure that operations can continue even if primary facilities or systems are unavailable.
Disaster Recovery Planning (DRP): The Disaster Recovery Plan focuses specifically on the restoration of IT systems and data following a disaster. It outlines the steps necessary to recover from various types of disruptions, ensuring that VADA’s technology infrastructure can be quickly restored.
Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO): The DRP defines RTOs and RPOs for critical systems, specifying the maximum acceptable downtime and data loss for each system. These objectives guide the design of recovery strategies and ensure that recovery efforts are aligned with business priorities.
Incident Response Integration: The DRP is integrated with VADA’s incident response plan, ensuring a seamless transition from immediate incident handling to long-term recovery and restoration efforts.
Regular Testing and Updates: VADA regularly tests and updates the BC/DR plan to ensure its effectiveness and relevance.
Simulated Drills: The organization conducts simulated disaster recovery drills and business continuity exercises to test the plan’s effectiveness and to train employees on their roles and responsibilities during a disruption.
Plan Reviews and Updates: The BC/DR plan is reviewed and updated annually, or whenever there are significant changes to the organization’s infrastructure, processes, or risk landscape. This ensures that the plan remains current and capable of addressing emerging threats and challenges.
2. Redundancy and Backups
Ensuring System Resilience and Data Protection: VADA implements redundancy and backup strategies to protect critical systems and data, ensuring that they can be quickly restored in the event of a disruption.
System Redundancy:
High Availability (HA) Architectures: VADA’s critical systems are designed with high availability architectures, using redundant nodes, storage, and components to eliminate single points of failure. This ensures that if one component fails, others can take over without interrupting service.
Geographically Distributed Nodes: VADA utilizes cloud providers with multiple availability zones, geographically distributed nodes to host its critical systems. This geographical redundancy ensures that services can continue even if one availability zone is impacted by a regional disaster.
Data Backups:
Regular Backup Schedules: VADA implements regular backup schedules for all critical data, including daily incremental backups and weekly full backups. These backups are securely stored both on-site and off-site to protect against data loss from node failures, cyberattacks, or other disasters.
Automated Backup Systems: Automated backup systems, are used to ensure that backups are consistently performed according to the schedule. These systems include features such as encryption, compression to enhance the security and efficiency of backups.
Backup Testing and Validation: VADA regularly tests and validates its backups to ensure that data can be restored quickly and accurately when needed. These tests include restoring backups in a controlled environment to verify their integrity and completeness.
Rapid Data Restoration:
Instant Recovery Solutions: VADA employs instant recovery solutions that allow critical systems and data to be restored within minutes, minimizing downtime and disruption. These solutions include the ability to run applications directly from backup copies if the primary systems are unavailable.
Cloud-Based Backup and Recovery: VADA leverages cloud-based backup and disaster recovery solutions as Azure Site Recovery. These cloud services offer scalable, on-demand recovery options that can be quickly activated in the event of a disaster.
Through its robust Business Continuity and Disaster Recovery planning, VADA ensures that it can maintain operations and quickly recover from any disruption, thereby safeguarding the interests of its clients and ensuring the ongoing availability of its services.
VIII. Audit and Compliance
VADA is committed to maintaining the highest standards of security and compliance through rigorous auditing processes and continuous improvement of our security posture. These efforts ensure that our security measures are effective, aligned with industry standards, and capable of adapting to emerging threats.
1. Internal Audits
Ensuring Ongoing Compliance: VADA conducts regular internal audits to verify compliance with our security policies and procedures, ensuring that they are consistently applied across the organization.
Scheduled Audits: Internal audits are scheduled at regular intervals throughout the year, covering all aspects of VADA’s security framework, including access controls, data protection, network security, and incident management.
Comprehensive Scope: These audits assess the effectiveness of current security controls, identify potential weaknesses or areas of non-compliance, and ensure that all employees and systems adhere to the established security policies.
Audit Tools and Automation: VADA employs automated audit tools to streamline the audit process, enabling continuous monitoring of security controls and generating real-time reports on compliance status.
Audit Reporting: Detailed reports are generated following each internal audit, outlining the findings, any identified gaps, and recommended actions. These reports are reviewed by senior management and used to drive improvements in the security program.
2. Continuous Improvement
Adapting to Evolving Threats: VADA is dedicated to continuous improvement, regularly updating our security measures based on audit findings, industry developments, and emerging threats.
Audit Findings and Remediation: After each audit, both internal and external, VADA reviews the findings and implements corrective actions to address any identified gaps or weaknesses. These actions are tracked to ensure timely resolution and are incorporated into our ongoing risk management efforts.
Security Program Enhancement: VADA’s security team continuously monitors the threat landscape, incorporating lessons learned from audits, new security technologies, and best practices into our security program. This proactive approach ensures that our security controls evolve to meet new challenges and that our defenses remain robust.
Employee Training and Awareness: As part of our commitment to continuous improvement, VADA regularly updates its employee training programs to reflect new security policies, procedures, and threats identified through audits. This ensures that all staff are aware of their roles in maintaining security and compliance.
Through rigorous internal audits, coupled with a strong focus on continuous improvement, VADA ensures that our security practices remain effective, compliant, and aligned with the best industry standards, providing our clients with the highest level of trust and assurance.
IX. Conclusion
1. Summary
VADA’s commitment to SOC 2 compliance underscores our dedication to maintaining the highest standards of platform security. By adhering to SOC 2 principles, we ensure that our security controls are robust, effective, and capable of protecting the sensitive business data entrusted to us by our clients. Our rigorous approach to access controls, incident management, and continuous auditing guarantees that we not only meet but exceed industry expectations for security, availability, and confidentiality.
SOC 2 compliance is not just a certification; it is a cornerstone of our security strategy. It provides our clients with the assurance that their data is managed with the utmost care, following stringent security protocols that are regularly evaluated and improved. This commitment helps us build and maintain trust with our clients, ensuring that they can confidently rely on VADA’s platform to support their business operations.
2. Future Plans
Looking ahead, VADA remains focused on further enhancing our security posture and compliance efforts. Our future plans include:
Advanced Security Technologies: We are exploring the integration of advanced security technologies such as zero-trust architecture, AI-driven threat detection, and automated incident response systems. These innovations will help us stay ahead of evolving threats and enhance our ability to protect client data.
Expanded Compliance Frameworks: In addition to maintaining SOC 2 compliance, VADA plans to expand our compliance efforts to include additional certifications and standards such as ISO/IEC 27001 and GDPR. This will ensure that we meet the highest global standards for information security and data protection.
Continuous Training and Awareness: We will continue to invest in employee training programs to enhance security awareness and ensure that our staff remains knowledgeable about the latest security practices and compliance requirements.
Client-Focused Security Initiatives: VADA will work closely with our clients to tailor our security measures to their specific needs, offering customized solutions that provide even greater protection for their data. We plan to introduce more client-facing security tools and dashboards, giving clients greater visibility into their data security and compliance status.
By continually improving our security measures and expanding our compliance efforts, VADA aims to provide a secure, reliable, and trustworthy platform that meets the evolving needs of our clients, helping them achieve their business objectives with confidence.
